Integrating AWS Security Hub and AWS Config: A Step-by-Step Guide to Automate Compliance
Last Updated on November 7, 2024
Quick Summary
This blog is a step-by-step guide on integrating AWS Security Hub and AWS Config for easier compliance management. We’ll explain how to set up your environment, configure AWS Config rules, and link them with AWS Security Hub. We’ll also highlight the key benefits and features of AWS Security Hub and AWS Config, showing how they can help automate compliance.
Maintaining compliance and a good security posture in a cloud environment relies upon achieving and managing it through automation with tools such as AWS Security Hub and AWS Config. AWS Config monitors and records resource configuration continuously, while AWS Security Hub aggregates and prioritizes security findings for multiple AWS services. This blog focuses on integrating AWS Security Hub and AWS Config to yield automated compliance management. We will focus on how AWS Config works at the rules level on resources while providing configurations to the AWS Security Hub that aggregates and analyzes security-related data giving a holistic picture of the state of security within the particular environment.
AWS Security Hub is an integrated service for security management that allows one to gain an overview of their AWS security posture. It aggregates and classifies all enabled AWS services security findings, including GuardDuty, AWS Config, and AWS Inspector, to track compliance and identify security risks in an AWS environment. AWS Security Hub will now aid you in automating how your environment will be evaluated against the best practices and security standards so that you can ensure continuity in maintaining security and compliance.
AWS Config is a service that provides an evaluation, auditing, and compliance report of your AWS resources’ configurations. It continuously monitors and records your resource configurations and allows for assessment at any time. These capabilities enable compliance with internal policies and regulatory standards. With AWS Config, you can discover existing resources and export a complete inventory of your resources with all detailed AWS configurations. By configuring AWS Config, you can target specific resources or types of resources, and you can set up the resource triggers that are used to detect changes. Also, you can use it to set up rules that automatically check that the changes to your resources are consistent with your desired configurations.
Let’s learn about integrating AWS Security Hub and AWS Config to check if your EC2 instances and S3 buckets follow the rules.
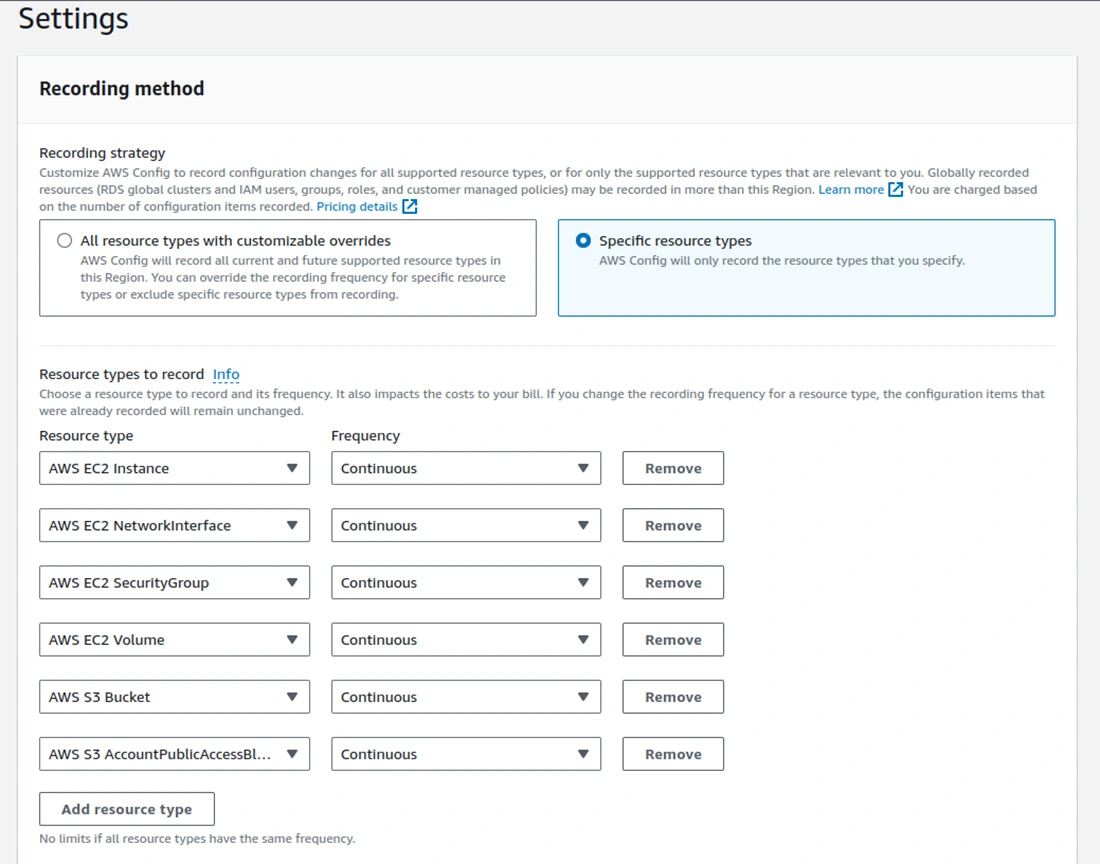
ec2-instance-no-public-ip – checks whether EC2 instances have public IP addresses.ec2-instance-detailed-monitoring-enabled – ensures that detailed monitoring is turned on to all the EC2 instancesec2-security-group-attached-to-eni – checks whether security groups are attached to Elastic Network Interfacesec2-instance-profile-attached – checks that EC2 instances have an instance profile attached to them.ec2-volume-inuse-check – ensures all EBS volumes are attached to an instance.restricted-ssh – checks for unrestricted SSH access.ec2-managedinstance-association-compliance-status-check – verifies whether EC2 managed instances are in compliance.ec2-ebs-encryption-by-default – ensures EBS encryption is enabled by default.encrypted-volumes – checks whether EBS volumes are encrypted.ec2-stopped-instance – verifies if there are any stopped instances.For S3 Buckets, select rules like:
s3-bucket-level-public-access-prohibited – checks whether EC2 instances have public IP addresses.s3-bucket-server-side-encryption-enabled – checks if server-side encryption is on or off for S3-buckets3-bucket-public-read-prohibited – confirms that S3-buckets are not publicly readable.s3-bucket-public-write-prohibited – ensures the S3-bucket cannot be written into from the public.s3-bucket-logging-enabled – this test confirms that server access logging is enabled on the S3-buckets.s3-bucket-versioning-enabled – it ensures versioning has been enabled for S3-buckets3-bucket-replication-enabled – it ensures that replication is enabled for the S3-bucket when it applies.


Integrate easily without any worries, leverage our AWS Integration Services, and let us handle the complexities.


To receive email notifications for AWS Config changes, you can configure an SNS topic.
1. First of all, create an SNS Topic:
SNSConfigTopic), then click Create topic.2. Create an Email Subscription:
3. Link AWS Config to the SNS Topic:

We have implemented a remediation process to start EC2 instances when they are stopped automatically. Here’s how you set it up:
1. Create a Custom IAM Role for AWS Config Remediation:
Trust Relationship Policy:

{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": [
"config.amazonaws.com",
"ec2.amazonaws.com",
"ssm.amazonaws.com"
]
},
"Action": "sts:AssumeRole"
}
]
}
Permissions for the Role:
2. To set up AWS Config-managed remediation, follow these steps:
ec2-stopped-instance.3. Test Remediation:

Therefore, integrating AWS Security Hub and AWS Config gives total visibility about the security posture, making decisions more effective and efficient regarding security management. You can always hire expert AWS developers to simplify compliance monitoring with actionable insights, automated alerts, and remediation-all critical to maintaining a secure AWS environment.
Your Success Is Guaranteed !
We accelerate the release of digital product and guaranteed their success
We Use Slack, Jira & GitHub for Accurate Deployment and Effective Communication.